Nowadays, we are bombarded with all kinds of cyber-attacks, which have become the main agenda and area of concern for every organization. All the investment in IT Security tools is focused on strengthening the external perimeter of the organization to deal with such attacks. Little that we realize that sometimes we overlook the importance of protecting our internal organization.
IT Security is about protecting the entire organization because the threats are not only coming from external, but we must also be wary of the potential threats from within the organization. Information and data protection are among the critical resources we need to safeguard because it involves the safety of our clients, compliance with the local regulations, and the organization’s reputation as an entity. This is what we believed in and has been in practice here at The ASCENT Group.
Internal Security Risks
Based on the “VARONIS 134 Cybersecurity Statistics and Trends for 2021”, it was indicated that 17% of the sensitive files in a typical organization are accessible by all the employees, and on average, the employees have access to 11 million files. This has clearly shown us how common the organization’s data is being handled by the end users every single day.
Emphasizing, even more, the same report indicated that 60% of these companies have more than 500 accounts with non-expiring passwords! You can just imagine the severity should be one of these accounts was compromised or fell into the wrong hands. It was also indicated that 77% of the companies in this report do not even have an incident response plan.
Source:https://www.redteamsecure.com/danger-ranks-7-times-employees-caused-data-breaches/
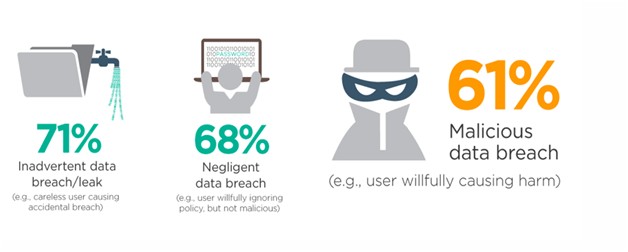
As you can see, the statistic shows that 71% of the cases were in the “Inadvertent data breach/leak” category, and the end users were careless or did not even realize that they had caused the data breach incident. The statistic showed us that 68% of them were aware but willfully ignored the policy, leading to data breaches. What we should concern about is the internal perpetrators or the unlawful conduct of our own employees leaking the organization’s data for personal gain. Don’t you think that 61% is a very worrying percentage? There are very high chances of happening, and the impact shall jeopardize the whole business.
Apart from the above, there are also many other internal risks, if not addressed, will have an impact on the organization:
- Resistance to technology change.
- Unskilled and lack training.
- Generation gap and culture.
- Unfiltered social media exposure.
- No sense of responsibility and ethics.
External Security Risk
I think the external risks would have a more significant impact because they are a force we could not control. This is unlike the internal risk that we can address and contain within the organization itself. The external threats may come in the form of cyber-attacks, manipulation, scams, or even industrial espionage.
If we take the cyber-attacks, for example, the number of attacks reported kept increasing year after year, and the organization is constantly at risk almost all the time. Furthermore, we could also see that of late, hackers and cyber-criminals have become more advance and creative in finding ways to penetrate organizations. So it is an ongoing challenge for IT Heads and CIOs like us to keep up with this evolving threat landscape.
While companies spend thousands on providing the right tools and IT Security infrastructure, all these efforts would be in vain should we not address the human factor in the organization. It is just like building a solid wall around your fortress, while the source of vulnerability comes from within. With all the firewall, intrusion detection, and preventions, the company was still hit by the ransomware attack simply because a user failed to follow the rule of not opening any attachment from an unverified source.
Identifying Potential Impact
All organizations should adequately assess the impact on the organization, should they choose to ignore the risks. As the saying goes, “Prevention is better than cure.” I am confident that the cost of incident recovery is much greater than taking a proactive step to prevent it from happening.
IT should work closely with the Management to manage the expectations and to work towards mitigating the following potential impacts:
- Identity theft – When a credential is stolen, the organization is left vulnerable to any kind of damage and manipulation. The impact would be worse should the stolen ID has a high privilege access right.
- Monetary theft – Be it paying to release the data from a Ransomware attack or your organization’s money is quietly being siphoned out from the company, the financial loss is inevitable.
- Cancellation of contracts – If your organization is a vendor to a big company, you may face a contract cancellation should they find out that your end users were involved in any unlawful conduct.
- The lawsuit (against you or your company) – This would add salt to the wounds should you need to face a case originating from an incident. The demand may either come from your contractors or your customers.
- Liabilities for fines and penalties – You may also be fined or penalized by the Regulators should such a data breach or violation happen in your organization.
- Reputation loss – All the effort and years of hard work in building your organization to where it is will go to waste if any of the incidents cause your organization to lose its reputation. You may not be able to recover from this at all.
Securing The Gaps
“Know what to protect; protect what you know.” As mentioned earlier, every organization has a lot of data and information they handle daily.
In ASCENT, we acknowledged that it would be almost impossible to protect everything with our limited budget and resources. Therefore, we must prioritize and apply for the strictest control and protection over your most valuable information assets.
Therefore, we believe that communication is essential for us to have support from everyone in the organization. They need to be involved in understanding these initiatives’ importance. One of the promising approaches was to apply the business users and to get their commitment as follows:
- Discover– Make sure the business users are involved in discovering all the company’s information assets, be it hardcopy or digital. As they are the Data owners, they would know best about the data being recorded or used daily.
- Classify– Once they list all the information assets in the company, let them classify and rank the most critical support they would like to protect. We can’t cover everything with limited resources; hence, organizing these data would help assign the proper protection to the most critical data.
- Enforce – This is where IT comes in and enforces all the necessary controls like the ACL to make sure only the authorized person would get access to these data. Since we have included the business from the beginning and they were the ones who defined which data to protect, it will be easier to get them to comply and accept.
The Top Management of ASCENT plays an active role and always keeps abreast with the overall IT development in the organization. This enables IT to have a clear direction and the proper support to implement the necessary controls and make an investment in IT Security Tools to mitigate all the risks that I have mentioned just now.
We believe that a good IT Security posture should have the balance of all the 3 elements:
- People – The doers who would carry out all the organization’s strategic plans. They must be consistently educated on the latest threats to prepare themselves for potential attacks.
- Process – All the documents, procedures, and guidelines need to be updated to avoid overlaps and make the process more efficient.
- Technology – The right tools that fit the organization are required to support the business and protect the overall business ecosystem. There is no such thing as a “one size fits all” kind of solution, and every organization has its own unique needs to be addressed.
With all the above elements in sync, we should be able to fully utilize the IT Security Tools to safeguard the organization. Proper execution of the Data Leakage Prevention (DLP) system and having convenient access to the right staff would put the organization in check for Internal Security risks. In addition, combining a continuous staff awareness training program and IT Security tools like Firewalls and an Email/Web Filtering system would reduce the probability of impact from the External IT Security Risk.
Nothing is perfect
IT Security is an ongoing journey and not a one-time exercise to be carried out to secure the organization. With the rapid growth of the threats landscape, all organizations should also need to keep themselves up to date, well informed, on the alert, be vigilant and always be ready to adapt to new technologies.
This will be our journey and ongoing effort to create a secured and trusted ecosystem for everyone to do business with ASCENT.
Author:
Ts. Saiful Bakhtiar Osman
Head of IT – APAC